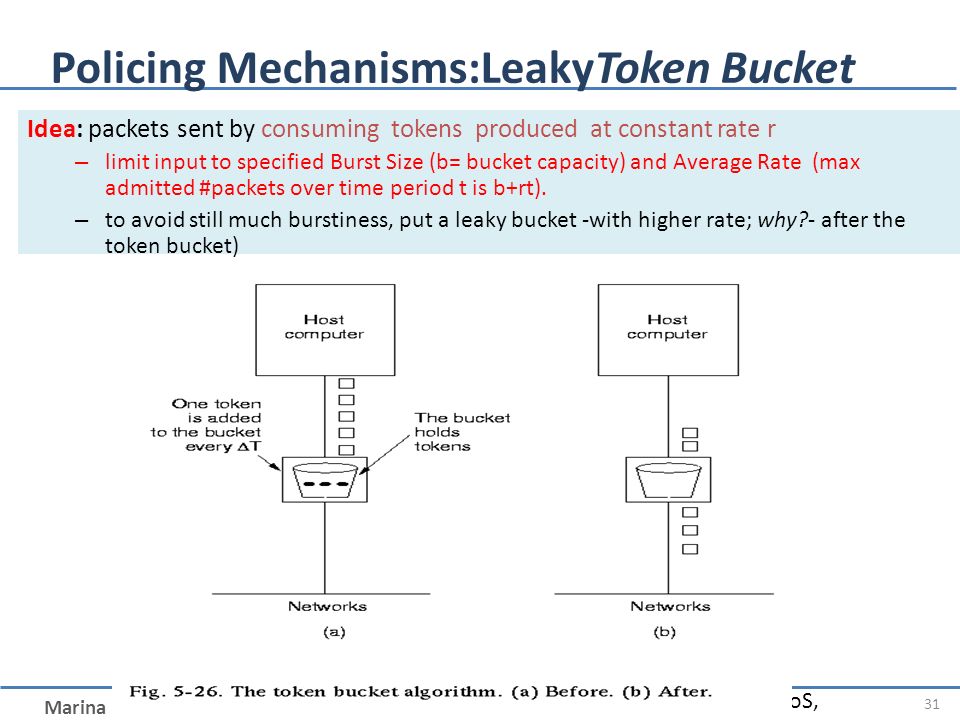
Course on Computer Communication and Networks Lecture 13 Chapter 7: Multimedia networking Chapter 3-5: VC-type congestion control EDA344/DIT 420, CTH/GU. - ppt download
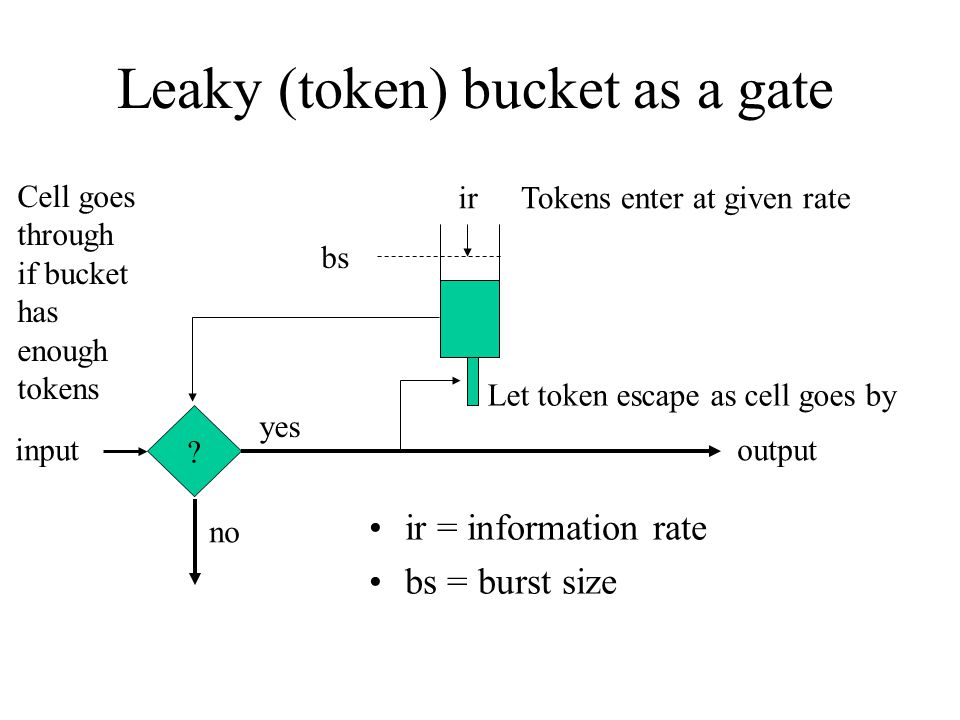
CS 4594 Broadband ATM GCRA and Leaky Bucket. From the ATM Forum The GCRA is used to define conformance to the traffic contract. For each cell that arrives. - ppt download

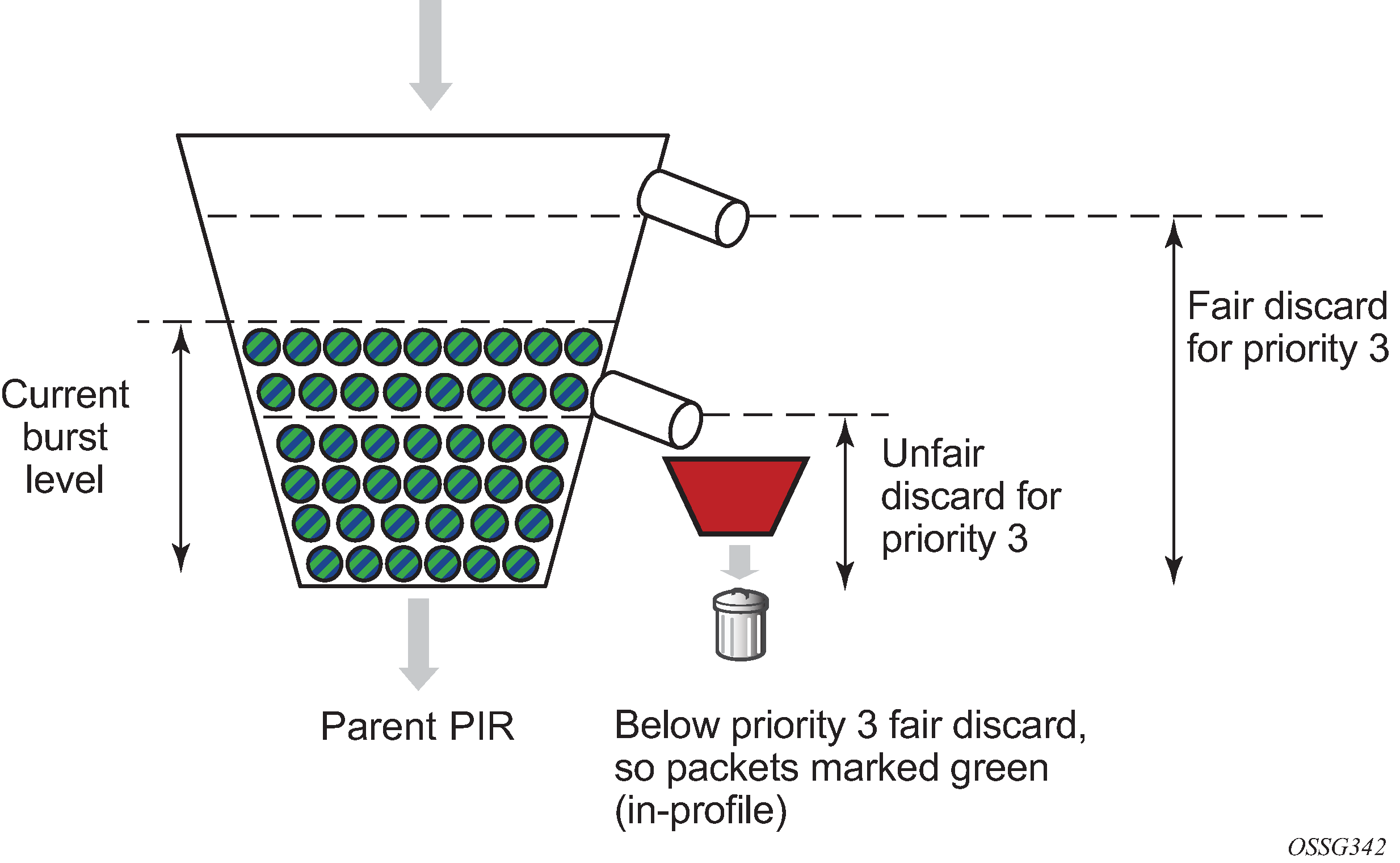






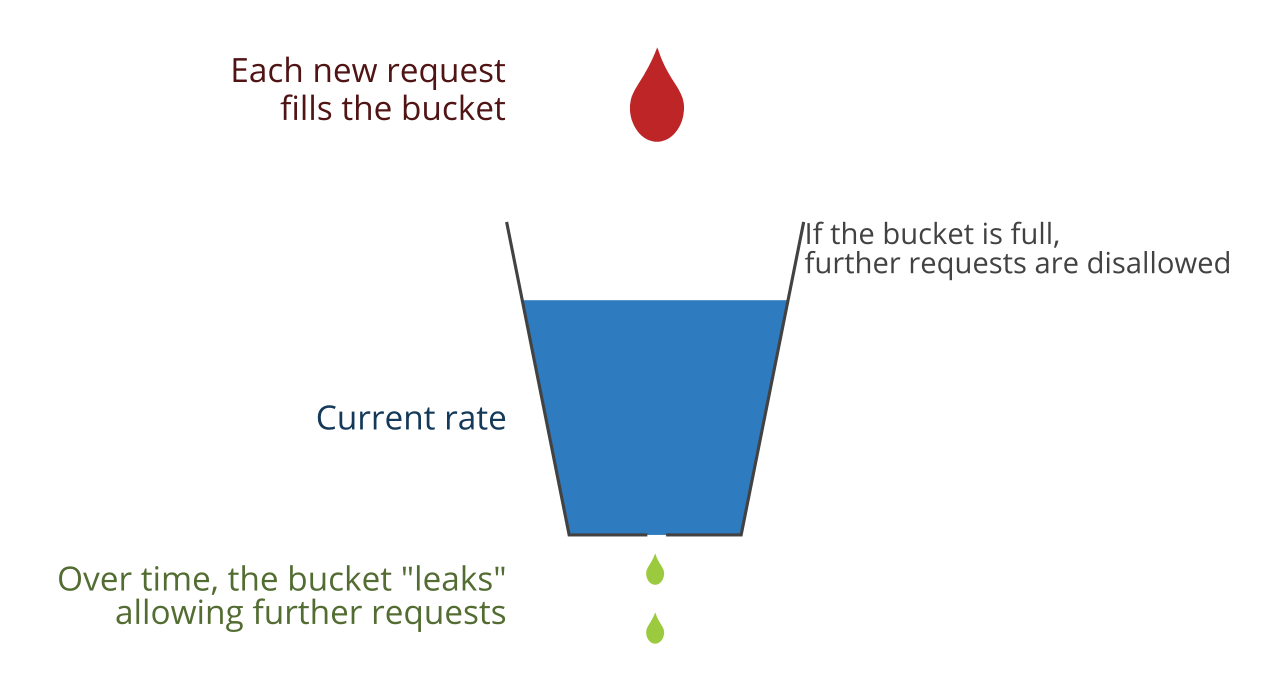

![4): A leaky bucket with packets [1] | Download Scientific Diagram 4): A leaky bucket with packets [1] | Download Scientific Diagram](https://www.researchgate.net/publication/325608278/figure/fig7/AS:634661147508752@1528326417212/Figure-34-A-leaky-bucket-with-packets-1.png)
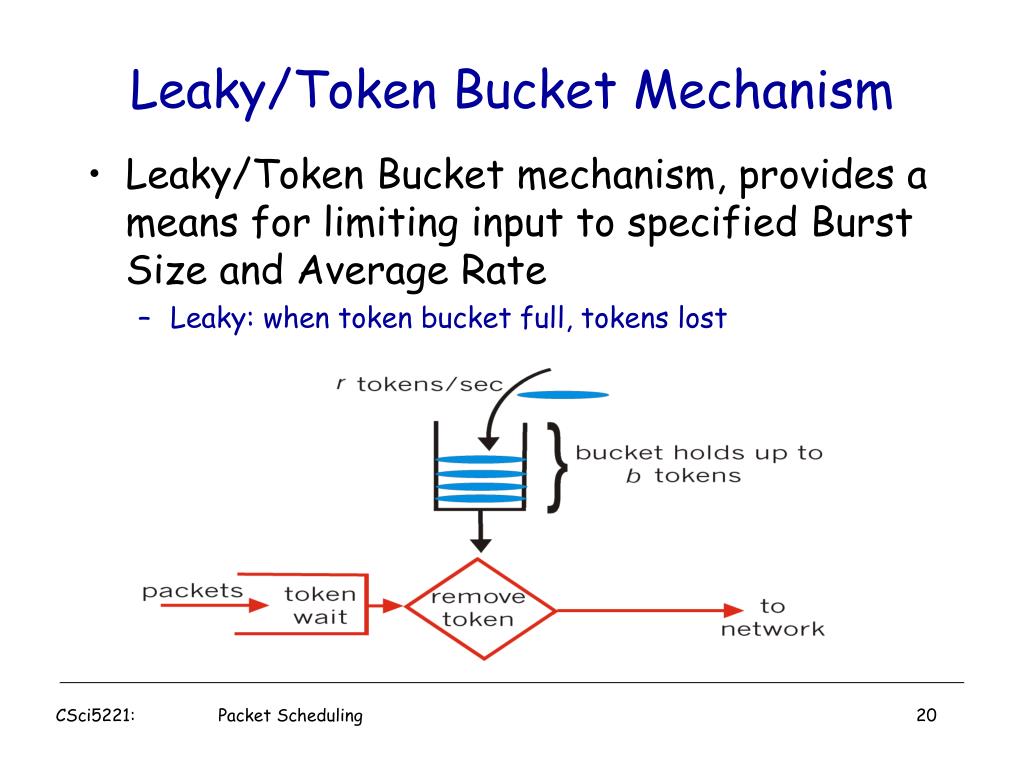

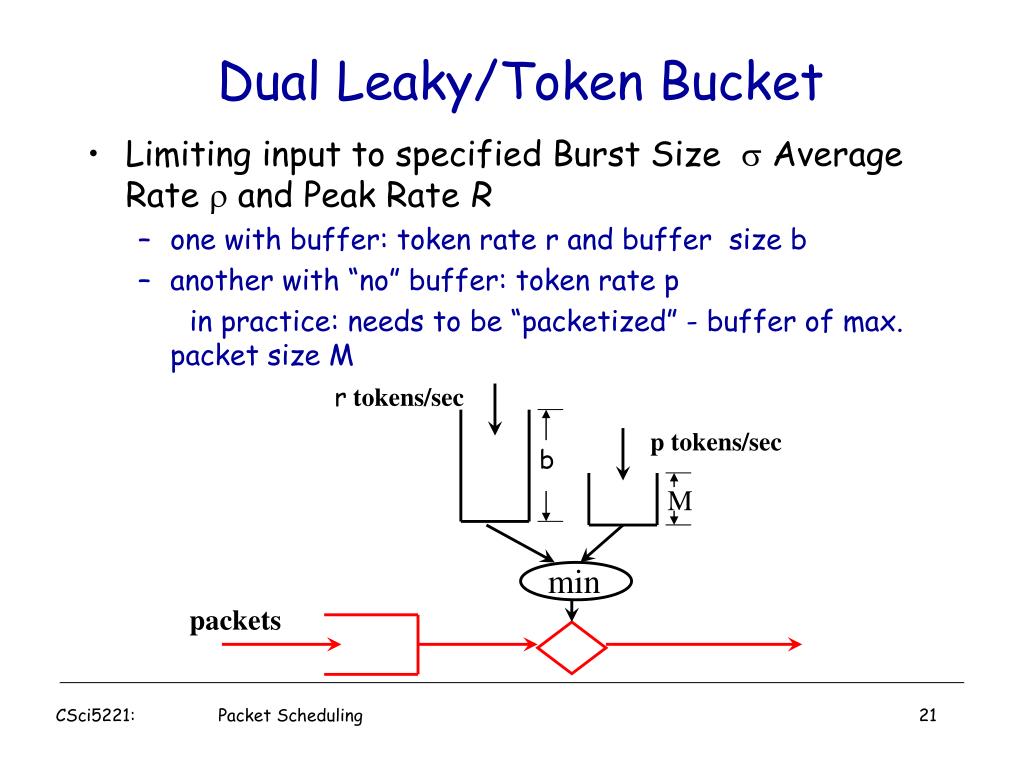

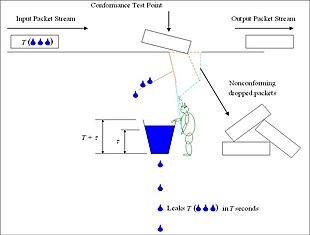
![5): The token bucket algorithm. (a) Before. (b) After. [1] | Download Scientific Diagram 5): The token bucket algorithm. (a) Before. (b) After. [1] | Download Scientific Diagram](https://www.researchgate.net/publication/325608278/figure/fig8/AS:634661147521024@1528326417356/Figure-35-The-token-bucket-algorithm-a-Before-b-After-1.png)

